The United Nation's Website Has a Massive WordPress Disclosure Vulnerability
The United Nations hasn't been having a good year as far as cybersecurity is concerned. They have been subject to two significant vulnerabilities, both of which may have resulted in personal information being leaked.
The first attack this year landed the UN in hot water. The attack involved the Trello board — a project management service — and scored hackers some internal communications and future plans as well as some UN members credentials. This hack was initially reported by Kushagra Pathak who has posted about Trello vulnerabilities in detail over on his Medium account.
Now, it's been revealed that a path and information disclosure bug in one of the UN's WordPress websites, gives unfettered access to job applications uploaded to the site since 2016. It’s believed that thousands of job applications containing private details about those who applied to UN-related jobs have been uploaded. Since this vulnerability has been around since August there's no telling how many people's applications were viewed by nefarious people.
Let's jump in and look at how hackers were able to penetrate the UN's website defenses and steal tons of private information at any time. As far as we know, this still hasn't been patched.
Step 1: Starts with WordPress
The attack was originally reported back in August, but the details are coming out this week. Mohamed Baset over at Seekurity uncovered the exposure initially but is just now releasing it after getting the run-around with the UN's security team. Apparently, the UN brushed the issue off a few times. Mohamed has a log of the details over on his website.
The problem here lies in a website where the UN sends applicants to upload their resumes.
Ok, so what? They used WordPress. That doesn't necessarily mean that the hack was related to WordPress. It could have been an employee accidentally leaking credentials, right?
Step 2: The story continues with WordPress
Well, unfortunately, the attack vector took advantage of an out-of-date WordPress flaw. The flaw is due to a misconfiguration in their WordPress architecture that has left files open to view to anyone who wants to see them.
The misconfiguration that caused the attack was a result of an open directory. As usual, the main advice given was "keep your WordPress website up-to-date." Which is definitely good advice. But, it highlights an unfortunate ongoing issue with distributed responsibility when using OSS, in this case WordPress, where blame and responsibility is being shifted onto Webmasters by WordPress.
It's this strange world where security firms want to tip-toe the line between outright blaming WordPress and blaming the webmaster. Usually, we see them sit in between. They don't want you to use another platform — they make a living off of WordPress.
Was the UN's website actually hacked? Maybe. Anyone in the world can go and view these people's personal information with little-to-no hacking skills. So far, no one knows how many people have seen these personal files. There is undoubtedly a built-in vulnerability. Often times, these security firms are the first ones to reach it (since they have just as much incentive as hackers to uncover weaknesses.)
Either way, this is a severe issue. There are thousands of uploaded resumes with personal information on them that anyone can take a peek into. Here’s a sample of a directory listing containing personal applications to UN jobs that Baset found on the site.
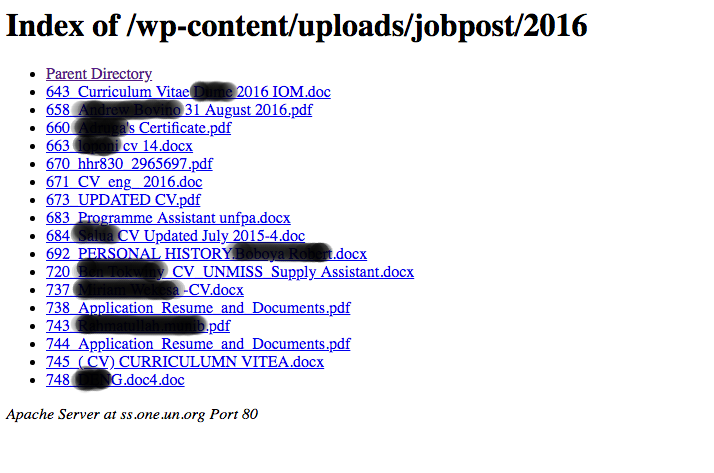
How It Happened
The United Nations was running their job application website using an Apache server with WordPress as the CMS.
The entire misconfiguration comes down to an open directory listing of wp-content/uploads. Essentially, a list of directory contents was left open allowing anyone to tap right into thousands of documents that were submitting by users looking to score a UN job. It's a simple bug, but it has some severe ramifications.
If you want to see a video of the "hack" in action, check out this YouTube video that was created by @seekurity.
It will be interesting to see what the result of this vulnerability is. Since information regarding the vulnerability was only released a few days ago, there hasn't been any big news yet, but with GDPR and consistently lingering regulations on private data leaks, we wouldn't be surprised if further action is taken.
It's also important to note that, since the UN's WordPress version is behind, it could be subject to further vulnerabilities.
How to Protect Your Website
With over 11,000 + vulnerabilities discovered so far, WordPress is definitely leaky. So, if you're running a website using WordPress, you may be wondering what you can do to protect yourself from hacks like the one that affected the United Nations.
Here are a few steps that you can take to help tighten up the security on your WordPress website.
- Keep up-to-date with WordPress security on goings.
- Keep your WordPress website version current.
- Don't make the mistake that the UN made here. Don't leave any directories open to the public.
- Make sure that the themes and plugins that you have installed aren't currently subject to vulnerabilities. WPScan Vulnerability Database is a great place to check up on current on goings with WordPress themes and plugins.
- Invest in cybersecurity elements — whether this is plugins, team members, or outside firms. If you use WordPress, you should definitely be spending money on security.
Honestly, even with cybersecurity elements, a fully patched website, and little-to-no plugins, you're still at risk. WordPress is not, and never will be, completely safe. This year, of course, has been particularly bad. Check out our post detailing the Sucuri 2017 Hacked Website Report if this UN vulnerability doesn't scare you.
Conclusion
This is just another in a series of unfortunate events for WordPress this year. We think that these types of "vulnerability reveals" are important to pay attention to. Not only does it give you some insight into how weak WordPress is at the moment, but it's also a great way to understand the underlying weakness in WordPress's open source nature.
You have security firms and hackers both rushing to find as many vulnerabilities as possible to make a profit. It's like a hacking gold rush. The result is a bunch of websites getting hacked and blame being shifted to Webmasters and Site Owners.
Are you tired of taking the blame for WordPress's insecure nature?
